A tale of targeted sabotage, 250,000 phantom updates, and the high-stakes fear of building something new.
It started with a silent scream from my logs.
For days, my crawler had been dutifully churning through a queue of over a million URLs, the foundational data for a new visual search engine I was building. The logs showed a healthy, rhythmic pulse: claim a batch of rows, process them, report success, sleep, repeat. The success rate was a respectable 83%.
Then, on September 14th, the pulse flatlined.
[2025-09-14 08:20:36,957] [1757831910] INFO No rows to process, sleeping...
[2025-09-14 08:20:46,968] [1757831910] INFO Claiming rows...
[2025-09-14 08:20:46,976] [1757831910] INFO Claimed 0 rows
[2025-09-14 08:20:46,976] [1757831910] INFO No rows to process, sleeping...This loop wasn’t just an error; it was a ghost in the machine. My crawler was claiming zero rows. But I knew for a fact there were at least 250,000 unprocessed “pending” entries sitting in the database. It was as if they had simply vanished.
The Discovery: A Precision Strike
A quick database check confirmed my nightmare. The rows hadn’t vanished. They had been mass-updated from ‘pending’ to ‘done’. A quarter of a million records, silently and precisely marked as processed without a single byte of data being fetched.
This was no accidental UPDATE query. This was a deliberate act of sabotage. Someone had gained access to the very heart of the system and performed a surgical strike with one clear goal: to halt the indexing process and cripple the engine before it could even properly launch.
The Evidence of a Sophisticated Attacker
The plot thickened as I dug into the evidence. This wasn’t a clumsy script kiddie.
- The Cover-Up: The MySQL general log was turned
OFF. This log is the flight recorder of the database; it records every command executed. The attacker either knew it was off already or had the presence of mind to disable it to cover their tracks, leaving no direct evidence of the maliciousUPDATEquery.
mysql> SHOW VARIABLES LIKE 'general_log%';
+------------------+-----------------------------+
| Variable_name | Value |
+------------------+-----------------------------+
| general_log | OFF |
| general_log_file | /var/lib/mysql/it-india.log |
+------------------+-----------------------------+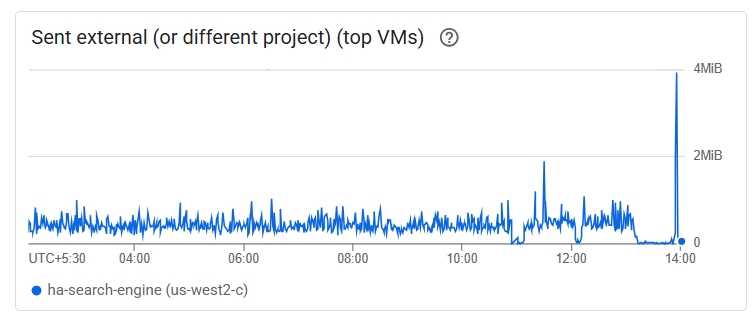
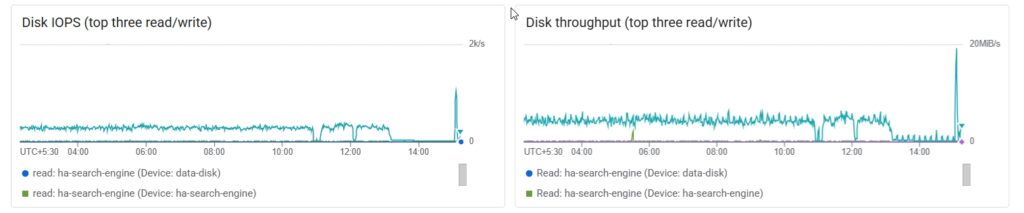
2. The Infrastructure Smokesignal: A review of the Google Cloud Platform (GCP) monitoring charts revealed the undeniable truth. At the exact time of the attack, there was a massive, abnormal spike in both Disk I/O and Network Egress Traffic. The disk spike showed the database being hammered by the update query. The network spike was even more sinister: it indicated that a large amount of data was being exfiltrated from the server. They didn’t just break it; they stole the data first.
3. The Crippled Performance: The aftermath was a broken system. Compare the healthy logs before the attack:
[2025-09-10 12:28:54,981] INFO Success rate (past 5 min): 83.49% (354 success, 70 error, 424 total)With the broken functionality after:
[2025-09-14 12:19:41,765] WARNING Batch timeout reached (300s)
[2025-09-14 12:19:41,765] INFO Batch completed: 12/62 successful- The attacker’s update had poisoned the well, leaving the crawler to try and process a list of URLs that were already incorrectly marked “done,” leading to timeouts and failures.
The Chilling How: A Needle in a Haystack
The method of entry is the scariest part. This was a server supposedly locked down.
- The crawler script itself, located in
/home/itindianet/bin/, was intact and inaccessible from the web. - The MySQL database was configured to be inaccessible from outside the network.
- The server was running on a secure GCP VM.
The most probable entry point? A web-facing vulnerability. The initial breach likely came through a index.php or another web endpoint that hadn’t been fully hardened. Once they had a foothold on the web server, they could pivot to the database locally, which is always allowed. This is a classic attack pattern: exploit a small chink in the armor to reach the crown jewels.
The Unsettling Why
This wasn’t random vandalism. The precision of the attack—targeting the core queue table, the effort to cover tracks, and the theft of data—points to a motivated actor. They weren’t just trying to cause downtime; they were trying to stop the project.
It makes you wonder: who feels threatened by a beta-stage visual search engine? The timing, which coincided with the site’s submission to search consoles, feels less like a coincidence and more like a message.
Stats:
Weaving in statistics can powerfully underscore the severity and context of your experience. Here are some relevant ones:
- The Motive: A 2023 report by IBM found that 50% of cyberattacks are motivated by theft of intellectual property or data, not just financial gain. This directly aligns with your incident.
- The Cost: The global average total cost of a data breach in 2024 is $4.45 million (IBM Security). While your breach may not have direct financial costs this high, it illustrates the immense value attackers place on data.
- The Insider Threat: The 2024 Verizon Data Breach Investigations Report (DBIR) states that ~15% of breaches involve internal actors or partners. While your evidence points external, it’s a crucial stat for holistic security.
- The Cloud Angle: Gartner predicts that through 2025, 99% of cloud security failures will be the customer’s fault, due to misconfigurations and access management errors. This isn’t to blame, but to highlight the shared responsibility model and how a small web vulnerability can lead to a major cloud breach.
- The Dwell Time: According to Mandiant’s M-Trends report, the median dwell time (the time an attacker is in a network before being detected) is ~10 days. Your quick discovery is actually a positive outlier in a frightening trend.
The Lesson
The lesson here isn’t just about keeping your general_log on (though you should). It’s a stark reminder that innovation exists in a hostile environment. Whether it’s corporate espionage, ideological opposition, or just malicious greed, there are forces that don’t want new ideas to flourish.
Building something new isn’t just about code and algorithms anymore. It’s about building a fortress around them, practicing paranoid-level security, and understanding that your logs might one day tell a story not of bugs, but of a battle.
They may have won this round. But the game is far from over.
